Introduction
Two Years After Being Unearthed, New Mandrake Spyware Plant is Found on Google Play Store Apps
Cybersecurity is a changing and increasingly critical industry, so to help users, as well as professionals, keep up-to-date with the new threats that emerge across security landscapes. The Unlucky Prospect How Federal Agencies Respond to Mandates and Report Vulnerabilities One of the most significant things you can do: Firewalls that hit performance, too New Volume Shadow Copy Service architecture provides file backups even when system restore points are turned off IRS watchdog has a problem with cryptocurrency reporting interfaces Using physical location as a factor in authentication? In the following, this article gets into Mandrake spyware further and sheds light on its return; what it does- how significant while offering people how to protect themselves.
What is Mandrake Spyware?
Mandrake spyware is a very advanced type of malware and was created specifically to penetrate in the mobile devices that are running on Google IAM operator’s services Android. This makes Mandrake different than any other malware strain out there especially given the fact that it was designed by some of the most advanced threat actors in business. The plundering is capable of performing a multitude of malicious errands such as :

Data Theft: Hacking to collect sensitive data like login access, bank details, and personal messages.
Remote Control: Obtain complete control over the infected device, thus allowing attackers to execute actions as if they were legitimate users.
Monitoring: Watching user’s actions or taking screenshots; Recording keyboard presses, and sometimes even listening to conversations.
THE RE-EMERGENCE OF MANDRAKE SPYWARE
A few years back Mandrake spyware was revealed which operated in the same way, effortlessly slipping past detection systems to bring ruin on any unlucky enough to be its target. Although cyber security scouts were relatively silent, a fresh outpour of Mandrake spyware contamination in Google Play Store apps is back. This Mandrake Spyware has been worrisome to some extent, given the long-standing threat from this malware and the problem of ensuring app marketplaces are secure.
How Mandrake Spyware Operates
Mandrake spyware has become increasingly sophisticated with its deployment in several stages and it takes a long time to raise the alarm. How Mandrake spyware usually works – an overview
Initial Infection:
Dissemination: Mandrake spyware usually comes loaded with otherwise innocent apps that can be downloaded from the Google Play Store. One of the telltale signs that spyware may be involved is if one or more apps seems like perfectly harmless utility tools, productivity apps, or games.
Mandrake Spyware Once installed the app will ask for a host of permissions, like many other apps do – something that users generally overlook or just blindly accept.
Dormant Phase: Hope Masquerading As Fear: For starters, the spyware injects itself into app code and lies dormant – often masquerading as more routine processes to avoid discovery. This is an important stage that makes sure that the user and security software do not catch you.

Activation:
Activation: At the scheduled time or remotely, spyware becomes active and functions occur.
Gadget Controller: it offers broader control over the device by utilizing the permissions landing this phone during setup.
Malicious Activities:
Data Exfiltration: The spyware starts to collect all the sensitive information and sends that back on the attacker’s server.
Remote Commands: Hackers can control an affected device by sending commands to Mandrake Spyware, which allows them to do various malicious actions such as stealing data or changing the way certain devices work.
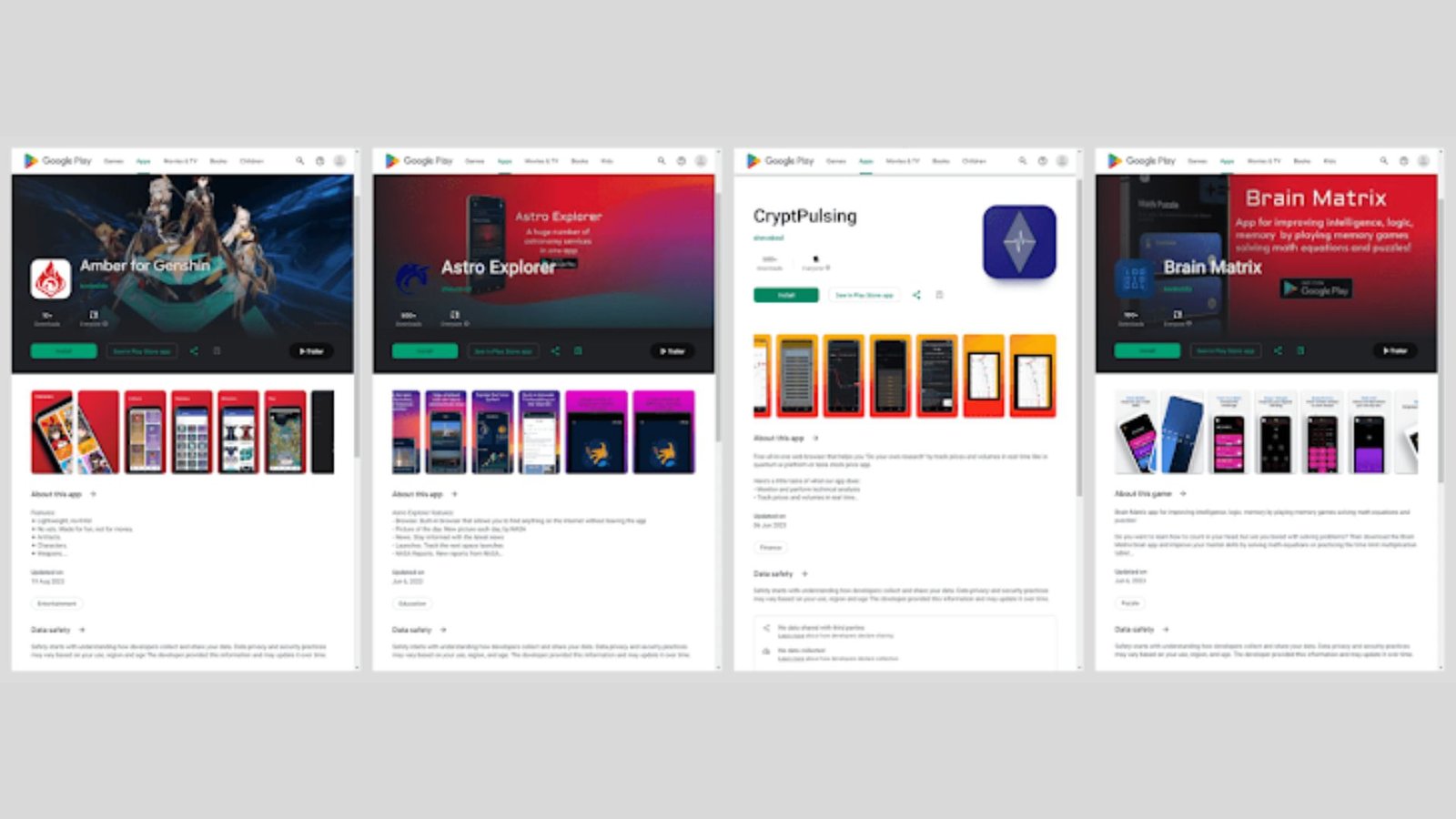
A new version of the advanced Mandrake Android spyware has been detected, this time in five applications that were accessible for downloading from Google Play and which went undetected two years later. Kaspersky said in a Monday write-up that the applications had attracted more than 32,000 installs between them before being yanked from the app storefront. Most of the downloads came from Canada, Germany, Italy, Mexico, Spain and Peru.”
The new samples featured additional layers of obfuscation and evasion methods to evade detection more effectively these included moving malicious functionality into obfuscated native libraries, using certificate pinning for C2 communications along with a larger range of checks whether Mandrake was running on a rooted device or emulated environment,” researchers Tatyana Shishkova and Igor Golovin noted.
Discovering Mandrake Romanian Cybersecurity vendor Bitdefender was the first to report on it in May 2020, laying out how the malware has been content simply contaminating a few devices over an extended period and evading detection since at least 2016. There is no indication that it points to a specific threat actor or group.
These newer versions feature the use of OLLVM to obfuscate the primary functionality and include a slew of sandbox evasion/anti-analysis techniques for this code not to be executed within environments run by malware analysts.
Below is the list of apps with Mandrake —
AirFS (com.airft.ftrnsfr)
Amber (com.sharp.sight)
Astro Explorer (com. astro. dscvr)
Brain Matrix (com. breath. matrix)
CryptoPulsing (com. crypto pulsing. browser)
The apps are distributed Mandrake Spyware in three stages: A dropper triggers a loader to download and decrypt the core malware component from a command-and-control (C2) server.
The second-stage payload can also gather information on whether the device is connected, installed apps, and battery level while others include the system’s external IP address and current Google Play version. It is also able to erase the core module and ask for permissions that will let it paint over other apps, or have activity in the background.
Third-stage available additional commands to load specific URLs in WebView and to start the writing session as well of remote accessibility overt with a spoof for recording device screen either on order if stealing user credential that, dropping nefarious application. Mandrake Spyware The new Android 13 ‘Restricted Settings’ feature prohibits sideloaded apps from requesting dangerous permissions directly,” the researchers said. According to Moinard, “To work around this limitation on the available RAM and CPU power Mandrake handles installation with a ‘session-based’ package installer.”
Mandrake is a prime example of this, with the Russian security firm painting it as a threat that’s still adapting and perfecting its tradecraft to slip past defensive layers and avoid detection. This demonstrates “the highly advanced capabilities of the threat actors, as well as how even more stringent vetting processes for apps before they are published to app store can mean that increasingly sophisticated and evasive threats still manage to pass through into official app marketplaces,” it added.
When contacted by Tools Near Me for further comment, Google provided the following statement: ‘We regularly carry out reviews of apps installed through official app markets to identify potentially harmful code and behaviors practiced in new forms; Play Protect is continually updated with improvements that allow it to better detect dynamically generated malicious content – additionally, we now also offer live threat detection capabilities which are used during obfuscation or anti-evasion attempts.’
If the device is running Google Play Services, then according to a spokesperson from Google “Google Play Protect automatically helps to keep users safe from this malware by disabling/removing impact app. Google Play Protect can alert users to or block bad apps even if they were distributed outside of the Play Store representing a necessary improvement.
You Can Read Another Blog: Check It




















